Background:
The infamous LockBit ransomware operation experienced a significant setback on May 7th 2025, when unknown attackers breached and defaced its affiliate login panels. The defacement featured a pointed message: “Don’t do Crime CRIME IS BAD xoxo from Prague.” However, the more serious blow came when the attackers leaked an SQL database containing multiple tables and datasets from LockBit’s administrative panel — an interface used by affiliates and administrators to manage ransomware operations.

Crime is bad - LockBit’s defaced leak site
Similarly, this appears to be similar to another breach of a ransomware group known as Everest who had their darkness site defaced last month Everest ransomware group's darknet site offline following defacement. Could this have been the same defacer?
Building on intelligence gathered during Operation Cronos, in May 2024, US and UK authorities formally revealed Dmitry Khoroshev—known by the alias “LockBitSupp”—as the primary administrator and architect of LockBit. He was charged in a 26-count indictment and named as the subject of a USD 10 million reward for information leading to his arrest. These developments marked a significant turning point in the global response to ransomware, exposing the leadership of one of the most operationally successful cybercriminal enterprises to date.
It seems the dump was taken around April although there are dump files dating back as early as December 2024; possibly the actor had a foothold for that long? Hard to tell but, given LockBit were taken down (from Operation Cronos), it’s odd that they would be as careless as to have an older PHP package from 2022, which includes RCE vulnerabilities. There are even more poor practices of OpSec found here.
LockBit SQL Dump Time
Users:
75 users in total were found from the list. Interestingly two of the users claimed to have been part of another group’s affiliates:
| User | Quote |
| BaleyBeach | 'We were affiliates of RansomHub, now RansomHub closed, we movede here. So existing companies (including yours) which we had to deal with still have chance to prevent their data leak.' |
| KoreyAllen | 'LockBit & HellCat encrypted your network. You have 39 days to negotiate.' |
Used for storing metadata related to ransomware builds, this dataset includes victim company domain names, with revenue amounts and dates. Over 630 unique domains are included, however, an ample amount are not actual victims, mostly being used for testing purposes.
It is possible to identify potential affiliate-operator relationships on the blockchain by analysing transaction patterns, particularly profit-sharing arrangements such as LockBit’s well-documented 80/20 model. In examining addresses linked to the user Christopher, we observe a consistent pattern aligned with this model: 80% of the ransom proceeds are directed to the affiliate, while 20% is allocated to the operator. Below are several examples demonstrating this behaviour, beginning with the receipt of ransom payments and tracing the subsequent distribution of funds.

Demonstration of 20:80 split from Crystal Intelligence
Despite users Matrix777 and admin appearing to be administrators, the largest contributors of messages are listed below. Christopher sent the largest amount of messages out of any, who we will discuss shortly:
Source: Valery Rieß-Marchive
Negotiations:
- This dataset contained invitation tokens and links that were sent to victims to initiate negotiations. Each invitation is linked to a Bitcoin or Monero wallet address, along with the amount of ransom demanded.
- The negotiation demands varied from as low as $4K to The negotiation demands varied from like $4K to $4.5M.
- Many victims also wanted to write in languages outside of English, highlighting the shift in targets geographically. Some correspondence expressed for negotiators to change language to communicate better with their victims: correspondence expressed for negotiators to change language to communicate better with their victims:
- “Can you speak Chinese? Writing in English is so hard.”
- “What is your mother language?”
However, LockBit operators maintained English throughout most negotiations with the exception of a couple of transcripts.
- Immature behaviours and inexperience were demonstrated amongst some operators:
- Asking to decrypt 1-2 servers and we actually see that in the transcripts. This is a technique that was seen in the earlier ransomware negotiation styles, not in a more established brand like LockBit. Something like this is indicative of inexperienced negotiators.
| Negotiator | Message |
| Victim | Brother, the final result of your price is that you won\'t get a penny, and the customer itself is a small company!' |
| Affiliate | 'I\'ve said it all' |
| Affiliate | 'price for 1 file 0.15btc' |
- Affiliates are still making silly mistakes going after CIS countries. Most Cyrillic-alphabet-language speaking ransomware groups are famous for having policies whereby they do not target countries who are members of the Counterparty of Independent (CIS) states. There have been many times where affiliates have accidentally breached a victim organisation from one of these countries. You can see this in one of the screenshots. I warn you the language is somewhat colourful if you translate but it’s a massive insight into what happens when a ransomware actor messes up.
Here is the transcript whereby an affiliate likely targeted a Russian-based org:
| Counterparty | Message Contents |
| A | "вы was hacked and via your account encrypted moscow target" |
| B | "what do you mean, what happened, what do you mean encrypted moscow target?" |
| A | "russian federation" |
| B | "I conducted my own investigation, it turns out that the adversary's account was hacked, the password in his account was changed, and then they locked you out. Possibly this is a special operation by the FSB to destroy my reputation or a setup from competitors." |
- Victims were also enticed by the RaaS program: ‘I saw from the ransom letter that I could pay $777 to join you? May I ask what benefits there are after joining? What needs to be done? Could you give me some information?' This comes from LockBit’s admin panel lite membership, which was mentioned in an interview with LockBit back in march from DeepDarkCTI:
- Q (Erez): Your Ransomware-as-a-Service (RaaS) model has been widely discussed. What measures do you take to vet potential affiliates and ensure they align with Lockbit’s strategic goals?
- A (Lockbit): Now, anyone can access a Ransomware panel and start working within five minutes after paying a symbolic fee of $777. Those who prove themselves as experienced pentesters will gain access to a more advanced and functional Ransomware panel.
- Q (Erez): Your Ransomware-as-a-Service (RaaS) model has been widely discussed. What measures do you take to vet potential affiliates and ensure they align with Lockbit’s strategic goals?
Further correspondence of recruitment and interest between victims and affiliates:
| Correspondent | Message |
| Ransomware Negotiator | '777 usd eto besplatnopoprosi u4etku v toxe dam besplatno bedolaga' |
| Ransomware Negotiator | 'we now have open registration in the panel lockbit, but it costs 777$.' |
| Victim | 'I saw from the ransom letter that I could pay $777 to join you? May I ask what benefits there are after joining? What needs to be done? Could you give me some information?' |
| Victim | 'If I make the payment within these two days, and also send the $777 membership fee to the same account, can I join you?' |
Furthermore, negotiation styles are very different across clients, the stylometrics indicate a difference of maturity across cases:
| Suspected Negotiator | ClientID | Initial Demand | Psychological Assessment of Full Negotiator Correspondence (Apply Magic Sauce - Prediction API) |
| 59X67 (36) | 112 | 110K USD | Age: 30 Psychological Gender: Masculine
|


Example (Opening Greeting)
since 2019 ~~~~
DO NOT WASTE TIME or your sensitive files will be PUBLISHED.
as you probably already know most of your systems are encrypted and data was stolen.
we stole ALL! databases and ALL! management shares from ALL! servers with sensitive data (total +4TB) on servers that are not encrypted too!
You can attach a few files for test decryption by packing them into an archive with zip, rar, tar, 7zip, 7z, tar.gz extensions of no more than 10 megabytes using the attach button directly in the chat.
Tell us filepaths and we will show proof of stolen data.
For security reasons we do not click on other links you send in chat.
Please wait for a reply, sometimes it takes several hours due to possible time zone differences.
We will offer decryption and deletion of all data for 110k$ in btc or 90k$ in xmr. price is suspect to change.
Upload to blog already started but we will stop after settlement.
do not waste yours and our time.'
| Suspected Negotiator | ClientID | Initial Demand | Psychological Assessment of Full Negotiator Correspondence (Apply Magic Sauce - Prediction API) |
| umarbishop47 (28) | 124, 77 | $50K USD
| Age: 38 Psychological Gender: Masculine
|





Example (Opening Greeting)
'Your network was penetrated, servers were completely encrypted with our special algorithm, and also we has downloaded sensitive Data from your file servers. In case if you won't cooperate with us, then everything would be published and/or sold. We also found a lot of contact information of your employees, clients, partners, etc. In case of your refusal to cooperate, we will try to convey information about the leak of your data to each of these contacts. We offer you to make a deal and resolve this issue smoothly, all encrypted files will be restored, you will avoid Data Leaks and we will provide you a proofs of deleting all your data from our server. The total weight of the files we have is approximately ~35 gigabytes. Price for all these services is $50,000 USD, it should be paid in cryptocurrency equivalent. - To prove that our Decryption tool works properly we can decrypt few random files for FREE, just send them to us - As a proof of data possession we can provide a partial file-tree of downloaded data (usually about 5-7% of total volume) You should also know that the files that were downloaded from you were carefully selected. These are not random files, but the most important ones in our opinion.'
| Suspected Negotiator | ClientID | Initial Demand | Psychological Assessment of Full Negotiator Correspondence (Apply Magic Sauce - Prediction API) | |
| Christopher (25) | 158 | hello, please wait | 35-30K | Age: 25 Psychological Gender: Feminine
|



Example (Opening Greeting)
hello, please wait
From this we can see a deviation in maturity of age, gender and even ways of thinking. Maturity and experience appear to be short with Christopher.
Furthermore, Christopher does not appear to have used washing techniques either. From a sample of the wallets provided:
Chat Snippet |
| hello, btc wallet: 1PKzZhK35fvszaHBdyAwHTRtEoJwjR1ocD |
| 1JTCt7wvKiBgT7rba5YZna8irfMvkacqFG |
| 1KNAZRC9ogEEE9doTggQomaswUGygaNDhS |
| 1BWbqn6xdFat3zLiaHPuFLqnZL7Q4obSKC |
| 1LZCdUhTZexZoRdS55wTcK1tAZrs8p7384 |
| 1BnSNSLk1zA3Jmcv6CMPqVmbMGwJrHThrp |
| Address: 1LZCdUhTZexZoRdS55wTcK1tAZrs8p7384 |
| 12ve4J9x4GYh7iHUpZxrVvz7XqkVn7MAaG |
| 14aVAxPaY22Nj4GpzChrJFWzoJyGSHi9az |

Crystal Intelligence - Tracking Christopher
The usage of WhiteBit and KuCoin are also similar to what we typically see with actors trying to withdraw their currency. A more experienced individual in this field would likely wash their funds to make it difficult to track their output, but not here. The issue here is that these wallets are only counterhops away from each other which is bad OpSec. Further reinforcing we are dealing with a more inexperienced user, or ‘script kiddy’.
Furthermore, they shared the exact BTC address ‘1BnSNSLk1zA3Jmcv6CMPqVmbMGwJrHThrp’ on two seperate cases. This is one of the biggest rookie mistakes we see across ransomware actors and fascinating that a LockBit affiliate is doing this.
Victimology was also an interesting one here. There were multiple targets to Chinese victims for low funds:
Correspondence from a victim |
| 'Hello, it is necessary for us to tell you about the current economic situation in China. The Chinese economy has declined by 40%, and the cost and tax of enterprise employees have risen sharply, resulting in insufficient demand and causing many small companies to be unable to survive.\nAs the designated negotiation agency of the client, we hope that your efforts will not be in vain and that you can also help the client complete the decryption. However, the cost is really beyond the client\'s affordability, and we hope that you can take a step back' |
| 'Yes, we have information about the finances of this company. We know for sure that this is not a large sum for them. In addition, many servers were encrypted. We will not discuss the economy of China here now. We are here only so that your client pays us and gets his data back.' |
| 'It\'s not that we don\'t want to talk, it\'s that the Chinese police don\'t allow them to do this. They have to spend their own money to do this, and in a sense it is also subject to government supervision. The customers really don\'t have that much money. Do you think 10,000 US dollars is okay? We will communicate and the deal will be done quickly.' |
Does this shift in victimology indicate desperation and difficulty in targetting groups? Well it could also be that affiliates are not actually certain who they are targetting. This is apparent where affilaite Christopher is corrected by one victim: “Bro, we are in Taiwan, not China. We hate China.”

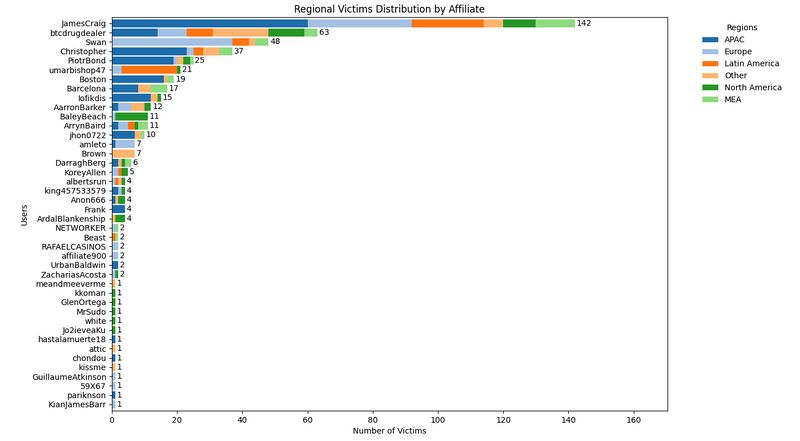
Valery Rieß-Marchive’s victimology chart - Valery Rieß-Marchive
We see in the above chart that LockBit’s targets are very much focused more on APAC than North America, signalling either a change of policy or the affiliates typically focus more on other regions outside of North America.
Case Study:
Crystal Intelligence - AB Capital
AB Capital:
Initial Contact and Data Proof
AB Capital: "Hi Lockbit, this is AB Capital and saw the post and may we ask to get the directory listing of all the files that you have. May we ask for more time so we can inform our stakeholders for them to assess and consider our next move? Lockbit: Thank you for understanding."
"you can download all the files that we have and see for yourself"
Further correspondence:
Dear Lockbit, may we state that last year was the only time we were profitable and we only earned $200k. We have also notified the regulators and our clients as well as required by law since the encryption last January 25 caused a major outage. That said, we were able to restore operation with some backups, albeit with some data loss therefore decryption wont really be necessary. Please give as an amount that we can get back to our leaders to be considered."
LockBit: "maybe we can lower the amount, but not by much."
"in the process of working with you, we thought about 100k."
"our principles have become worth more than money. However, a discount can be negotiated."
AB Capital: "Thank you for your consideration. 100k is still very steep for us as its half of our revenue which will be negated with the damage caused by the outage. May we respectfully ask to please significantly bring it down since we are only technically be requesting for the deletion of the data.
Final output:
LockBit: "I consulted and asked for another discount for you, our price will be 70k"
"and we will not rush you to pay"
"your office will allow you to pay that amount"
AB Capital: "Thank you for your concern and consideration, yes this funds will not be coming from IT. But we only have one owner, as we are a small private company, and he will have to cover everything. We will come back to you if we can convince him to pay 50k as this is still big for one person."
LockBit: "in the message in Viber there was a link to your archive to make sure"
"our price was 70k you write about 50k, let me talk to the team and agree on 60k for everyone"
"we agree to 60k, decision is yours"
AB Capital: "Will relay this and come back with a decision tomorrow morning as its 1am here."
Finally they agree to 40K USD:
| Correspondent | Chat |
| Victim | 'We would like to mention that we bought 40k USD worth of bitcoin this morning but with the volatility and transaction fees it will be less. Hope this is okay with you as we want to complete the transaction. Rest assured that we will give you all the btc we were able to acquire.' |
| Operator | 'ok' |
| Victim | 'Test transfer of $100 worth of btc has been sent to your btc address and is now PENDING in status. Please confirm once received. Thank you.' |
| Victim | 'The status of the test transfer is now COMPLETED, could you please check on your end?' |
| Operator | '+' |
| Operator | 'test transfer came' |
| Operator | '0.00124505' |
| Operator | 'you can send all amout' |
| Victim | 'We would like to split the next transactions in case we make a mistake. We will next transfer 20k usd in btc first and then the rest of the amount. We hope you understand and this is okay with you.' |
| Operator | 'yes of course, ok' |
| Victim | 'Split transfer of $20k worth of btc has been sent to your btc address and is now PENDING in status. Please confirm once received. Thank you.' |
| Victim | 'Could you help me a bit, may I ask the details of how you got access to our network? Did you exploit our public web app server or phish our users?' |
| Operator | 'is fine, 20k confirm' |
| Operator | 'remove the admin from the domain who controls infostructure, no matter what antivirus you install, the domain will always be vulnerable' |
| Operator | 'got to you through phishing, but I don\'t remember the first host' |
| Operator | 'and you had very easy passwords' |
| Operator | 'I followed the work Glen Moyo, and waited for him to log into Google Backup' |
| Operator | 'about a month' |
| Operator | 'sorry can you transfer the rest, i\'m very late now' |
| Operator | 'I need to go and I\'ll be here in a few hours' |
| Operator | 'Within 24 hours your archive will be deleted from the blog, also i use software http://heidi.ie delete archive from physical pc\nI\'ll send you a screenshot, you don\'t have to worry, we won\'t bother you anymore and your data will be securely deleted' |
| Victim | 'Sorry just wanted to clarify does this mean you were able to get glen moyo\'s account through phishing as well? ' |
| Victim | 'We are now sending the rest of the payment. Thank you for your response.' |
| Victim | 'Rest of the payment has been sent to your btc address and is now PENDING in status' |
We see the test payment being sent here, followed by the two splits of $20K outlined in the above transcripts:

Crystal Intelligence - AB Capital sending funds
And interestingly, the revenue generated to LockBit are split 20%, 20%, 35%, 25%:

Crystal Intelligence - LockBit splits
After paying they proceed to give them the root cause of entry: 'we got into the network through a manager with user priv, and dump ntlm local admin access on all the hosts in the domain'. So it is VERY likely that one of these contributors is to an initial access broker, possibly a dark-web forum selling such access.
Payments:
There are only two actual payments that were above 100k$ with 5 below 10k$, and 6 between $10-100K. The amount paid over the period is ~615000 USD, with an average of 41k$.
Moreover, less than 10% of negotiations actually led to payments which goes to show that the LockBit RaaS system isn’t thriving. Partly because these guys are going after low-hanging fruit where it's cheaper for victims to rebuild from scratch and/or the real professionals have shifted elsewhere. This also signals a shift in affiliates; there appears to be less going after Big Game.
Further Findings:
- The largest demand in the period from December 2024 - May 2025 was $4.5M USD as recent as 25 April
- There are transcripts where LockBit has allowed one-off payments for singular impacted systems to be decrypted. This is unheard of as they are a mass-franchised brand requiring multi-stakeholders, with each target costing sometimes up to $500K just for initial access (not to mention all the other fees for infrastructure hosting/affiliates/negotiators/crypto washers), a weird ‘good-faith’ practice that you don’t see from the bigger groups.
- Cloud: It doesn’t appear that the ~40 victim negotiations appear to be related to Cloud/Bucket-encryption-style ransomware attacks and still mostly targeting on-prem ESXI services and purchasing access via Initial Access Brokers (IABs). But just because LockBit doesn’t do this doesn’t mean other groups do not. Groups like BianLian have famously shifted primarily to exfiltration and groups like CodeFinger focus primarily on encrypting S3 buckets Codefinger ransomware encrypts Amazon S3 buckets. Its clear however ESXi/VMDK are a larger focus point for LockBit.
Sample messages |
| '1. there will be no problems with the decryptor,for esxi and all windows files\n2. you will need to disable your av and just run the .exe decryptor\n3. it could be someone else\n4. you know your pass P@ssw0rd' 'the VMDK files cannot be decrypter with the .exe decryptor. could you please send decryptor for VMDK in ESxi based on the txt file i sent you 15 minutes ago ?' 'Procedure for decrypting ESXi:\n- log in to vCenter\n- enable ssh access to ESXi\n- upload decryptor to ESXi via WinSCP or FileZilla; navigate to /tmp folder\n- login to ssh with root privileges\n- set permissions to run the decryptor with the command - chmod 777 decrypt\n- launch decryptor ./decrypt\n- follow the first method of decrypting by viewing the log file: tail -f /tmp/decrypt.llg, wait for the message at the end of the log - Your system is decrypted\n- the second way is to check the presence on the disk file decrypt.pid command ls, which protects the decryptor from the restart\n- the third way - ps | grep decrypt, as soon as decrypt.pid will be removed from the disk, or decrypt will disappear from the running processes, decrypt is complete\n- check the decrypt.llg log file and see the message at the end that the system was successfully decrypted \"Your system is decrypted\"\n- turn on virtual machines in ESXi\n\nYou cannot run multiple copies of a decryptor at the same time. After launching, the decryptor deletes the executable file and is demonetized, so that you cannot run the decryptor again and damage the files, this is normal.\n\nIf you have more than one ESXi host then you should not run the decryptor on all hosts simultaneously, make the decryption alternately, in the case of simultaneous operation of two decryptors may corrupt files and not be able to decrypt\n\nIf any files in another folder stay crypted, please use this command with path\nExample:\n./decrypt -i /tmp/files1/' |
| 'Procedure for decrypting ESXi:\n- log in to vCenter\n- enable ssh access to ESXi\n- upload decryptor to ESXi via WinSCP or FileZilla; navigate to /tmp folder\n- login to ssh with root privileges\n- set permissions to run the decryptor with the command - chmod 777 decrypt\n- launch decryptor ./decrypt\n- follow the first method of decrypting by viewing the log file: tail -f /tmp/decrypt.llg, wait for the message at the end of the log - Your system is decrypted\n- the second way is to check the presence on the disk file decrypt.pid command ls, which protects the decryptor from the restart\n- the third way - ps | grep decrypt, as soon as decrypt.pid will be removed from the disk, or decrypt will disappear from the running processes, decrypt is complete\n- check the decrypt.llg log file and see the message at the end that the system was successfully decrypted \"Your system is decrypted\"\n- turn on virtual machines in ESXi\n\nYou cannot run multiple copies of a decryptor at the same time. After launching, the decryptor deletes the executable file and is demonetized, so that you cannot run the decryptor again and damage the files, this is normal.\n\nIf you have more than one ESXi host then you should not run the decryptor on all hosts simultaneously, make the decryption alternately, in the case of simultaneous operation of two decryptors may corrupt files and not be able to decrypt\n\nIf any files in another folder stay crypted, please use this command with path\nExample:\n./decrypt -i /tmp/files1/' |
| 'Since we have several ESXI machines, one of them seems normal, but the number of virtual machines on that one is not large. Moreover, we have a NAS with a lot of office documents that we want to decrypt. Considering the current situation, I would like to communicate sincerely with you. You take the money, and we will try to minimize the loss of some data. Is that okay' |
- Their security-best practices for credential management are awful as they store affiliate credentials in plain text and permit users to use very basic passwords such as 'Lockbit123' (see below)
Username | Password |
| 'admin' | 'gyCuCzeMxHpT7a5fSYRDY5DxzefrdD5g5ktiibyE' |
| 'matrix777' | '81jlXQFHOdGiY8C3peSZxFUxtUKjbIhh1936k6xo' |
| 'fedor' | 'rYYBqlru7Wdp3VOAW9PJ' |
| ‘white’ | ‘Lockbit123’ |
| ‘godsjp’ | ‘Lockbitproud231’ |
- Root causes of most of these incidents are either from credential brute forcing, payload phishing, VPN exploits (FortiVPN to be exact). Also interesting to see them recommend taking down a Kaspersky Server without any context as to why: “You have a Kaspersky server in your domain, remove it”. Perhaps a zero day vulnerability?
Security Blue Team’s Observations:
- Are LockBit just in a grab-and-go phase? Will their name live onto LockBit 5.0? It's very doubtful after seeing the bar for entry so low within their affiliates.
- Exit Scam or Legit Hack? Groups like to fake their deaths to rebrand into other groups when the heat is too high. This typically happens if they are genuinely too good at their jobs, they hack critical infrastructure or the world wants them thrown in a Supermax prison. This also happens if there are internal conflicts for geopolitical reasons (e.g., BlackBasta & Conti). For Lockbit this has been a very long time coming. Dmitry Yuryevich Khoroshev who is famous for being the admin of Lockbit (aka LockBitSupp) still has a $10M bounty on his head from the US Department of State, with the NCA/Interpol and FBI all wanting their piece. Some of these zip files are timestamped back to December which begs two questions: (1) Was the perpetrator who hacked this website in since December? (2) If so, how did they remain undetected for this long? LockBit has been hacked before by law enforcement so to this seems very careless (no lessons learnt).
- They may return but during the time of writing (May 20th, 2025) there has not been another known victim on their leak site.
Closing:
If you are interested in analysing this further we recommend downloading the SQL Database from the following GitHub page rather than the dedicated leak site. Please do not do this on company laptops and only in a virtual machine where your host is safeguarded by antimalware. This has now been shared on GH: GitHub - WellKnitTech/LockBitPanelDB: Repo of the SQL database from the LockBit panel being hacked - Please take care in your analysis.
There’s so much to find from this and if you’re interested in negotiation techniques/tactics, the transcripts (after anonymisation) will be on Ransomchats Viewer.
Hudson Rock have also released a GPT Agent for this, ChatGPT - LockbitGPT. It hallucinates quite a bit as the reading time of GPT Agents are restricted so you won’t get all the answers to your questions however it is great for trend analysis.
The best approach still is to manually read and also run tooling to visualise keywords such as usernames, attack vectors, crypto wallets and all the rest. This of course takes time but you’ll inevitably find intel that no one else has discussed.
This topic will be explored further in an upcoming lab in our Ransomware: Negotiation & Threat Intelligence course.