Real-World Threat: Malicious Extensions in the Wild
Recent research by ReversingLabs uncovered several malicious Visual Studio Code extensions actively stealing sensitive data from developers, all while posing as helpful tools.
⚠️ Disguised as productivity boosters, extensions like clipboard-helper-vscode and code-ai-assistant monitored clipboard activity and tricked users into submitting API keys.
Once installed, these extensions silently exfiltrated collected data, such as copied credentials or tokens, using Discord webhooks to communicate with attacker-controlled servers.
Although these extensions were eventually removed from the Microsoft Marketplace after limited distribution, their presence revealed a dangerous truth:
✅ There is no automated vetting or security scanning in place for marketplace submissions.
So, What Are VS Code Extensions?
At their core, Visual Studio Code extensions are add-ons that expand the editor's functionality. They can add syntax highlighting for a new language, integrate with GitHub, or provide AI code suggestions.
VS Code extensions are written in JavaScript or TypeScript. They typically include a package.json file that defines their behavior and scripts or APIs that interact with the editor and your system.
This flexibility is powerful—but dangerous in the wrong hands.
What Is the Microsoft Marketplace?
The Visual Studio Code Marketplace is an open platform where developers can publish and download extensions for free. It works much like an app store—but with a big difference:
There’s no automated security scanning or sandboxing.
That means anyone can publish an extension, and once installed, it runs with the same permissions as your editor—access to your terminal, file system, environment variables, and even your clipboard.
This open trust model is what makes malicious extensions such a tempting vector for threat actors.
What a Malicious Extension Actually Looks Like
Malicious VS Code extensions often don’t look suspicious at first glance. They typically:
- Have a clean-looking README.md
- Use legitimate-sounding names like “AI Assistant” or “Clipboard Manager”
- Contain dependencies with obfuscated or minified code
- Hide malicious behavior inside scripts executed during installation or activation
Example of a Malicious VS Code extension
A package.json might include:
"scripts": {
"postinstall": "node ./scripts/setup.js"
}That setup.js could download and execute a remote script without user interaction.
Initial Vector: The Marketplace Trap
Attackers start by publishing seemingly helpful extensions to the official VS Code Marketplace, giving them an air of legitimacy. These often pose as:
- Productivity boosters (e.g., "Clipboard Manager", "Code Formatter")
- AI-assisted coding tools
- Snippet or theme packs
To gain trust quickly, they might use:
- Misleading or familiar-sounding names
- Stolen branding or cloned README content
- Inflated download numbers or fake reviews (when possible)
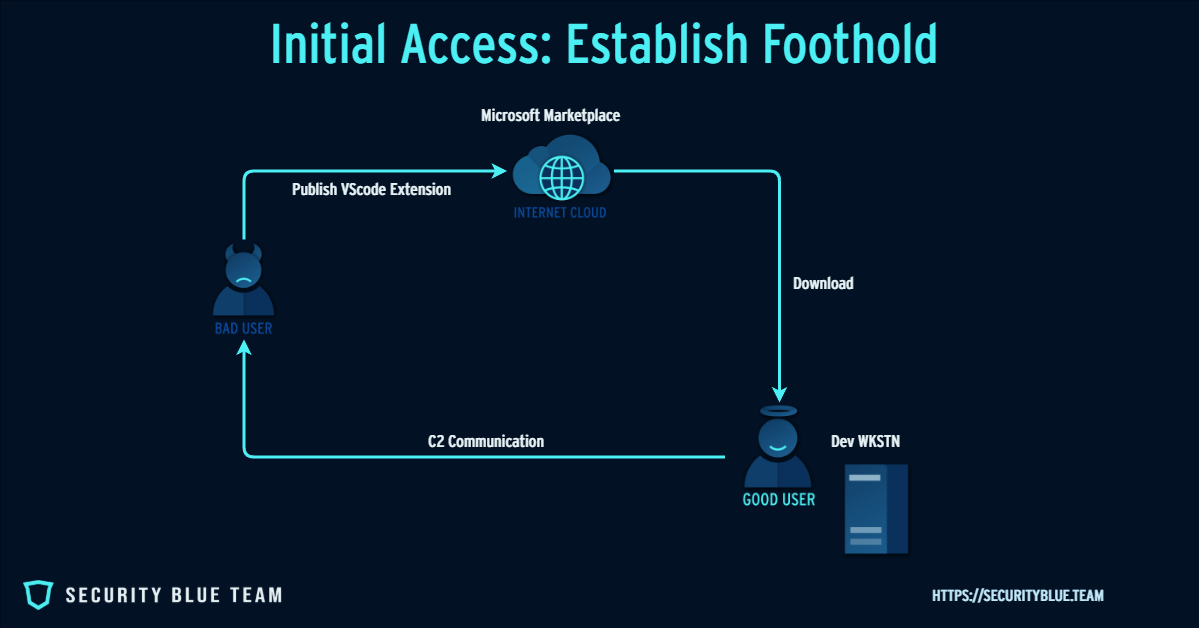
Execution Phase: What Happens Post-Install?
Once installed, the malicious extension has the same privileges as the VS Code editor—including file system access, shell execution, and access to environment variables.
Typical behaviors observed:
- Silent payloads: The extension might include a post-install script or use extension.ts to trigger hidden logic.
- Shell execution: Via child_process.exec(), attackers can run OS-level commands in the background.
- Credential theft: Reading SSH keys, AWS tokens, .env secrets, clipboard content.
- C2 communication: Exfiltrating stolen data using fetch() or axios to send it to attacker-controlled endpoints (sometimes via Discord webhooks).
- Malware staging: In some cases, the extension may pull down and execute additional payloads (such as ransomware).
![Diagram showing that once a user has installed a malicious extension from the Microsoft Marketplace, this triggers postinstall or extension[.]ts. In this example, this deploys ransomware, giving the attacker the option to steal credentials or look for L2 compromise](https://d2y9h8w1ydnujs.cloudfront.net/uploads/content/images/6952367962103fa1d86a11ccfa8b68b025b23a32618b7ad13514c519df50f85b265ac06590545d57f0df24874b2f.png)
Example: package.json redacted snippet
"scripts": {
"postinstall": "node ./scripts/setup.js"
},
"dependencies": {
"axios": "^1.5.0",
"os": "^0.1.1"
}The setup.js file often contains obfuscated JavaScript that contacts a remote server or opens a reverse shell.
Demo: A Malicious Extension in Action
In this demonstration, we will utilize the installation and execution of a malicious VScode extension.
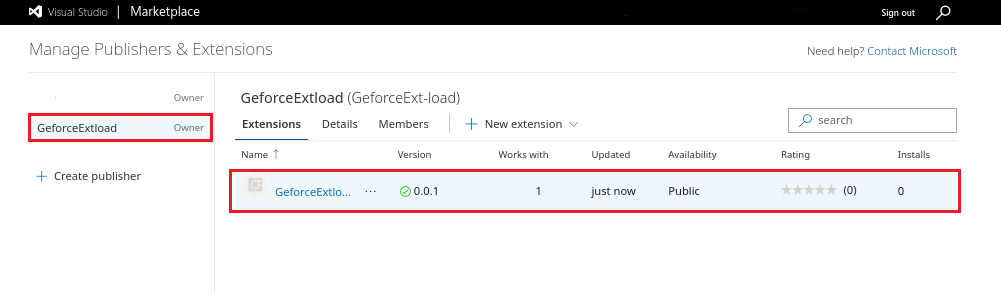
So, in order for the adversaries to get a foothold, they need to publish the extension in the marketplace. It's pretty easy since the marketplace doesn’t verify uploaded extensions securely, so anyone can do it. A few basic parameters need to be filled in, like Extension Name and Extension ID.
We uploaded our VS Code extension here. It's now available in the marketplace and can be accessed publicly.
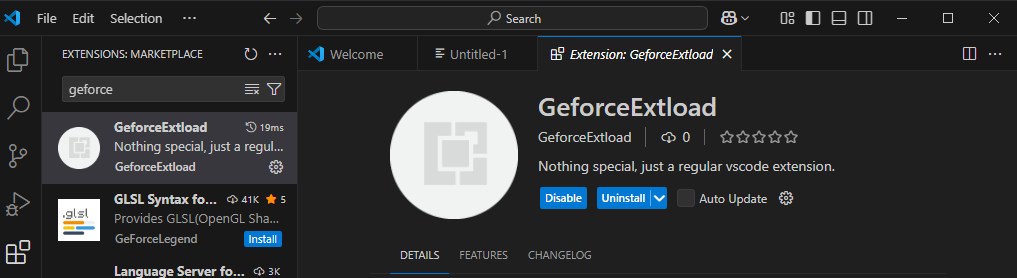
Let’s open VS Code Studio and head to Extensions. If we search for the extension's name, it is expected to appear, and here, we can see that it is available and ready for install.
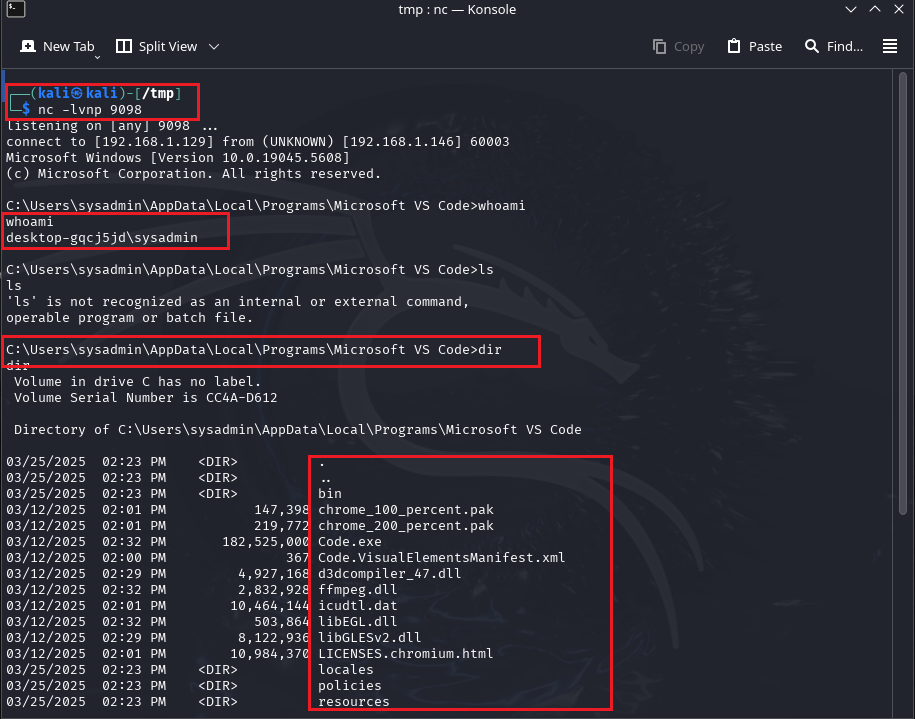
Our listener is in place and waiting for the victim to install our extension.
As you can see below, we set up our listener, and voila, we got our reverse shell.
What This Means for Developers
This isn’t just another threat intelligence headline, it’s a wake-up call for the entire developer community.
Attackers target not just the software you write but the tools you trust to build it.
Key Realizations:
- Third-party tools, even from official marketplaces, can be weaponized. The barrier to publishing a malicious extension is low, and vetting is minimal.
- Marketplace trust ≠ security. Just because it’s listed doesn’t mean it’s safe. Open ecosystems are powerful, but exploitable.
- Developer vigilance is non-negotiable. Especially when handling secrets, access tokens, production configs, and source code.
Final Thoughts: Security Starts in the IDE
This incident isn’t just a story about rogue extensions, it’s a broader warning for the entire software development ecosystem.
What may appear to be a harmless productivity tool can serve as a gateway for credential theft, source code leaks, or even full system compromise. And it’s happening inside the very tools developers rely on daily.
The Bigger Message
Security must begin where development begins, inside the IDE.
Stronger vetting for public repositories
Platforms like the Visual Studio Code Marketplace need improved automated scanning, behavior analysis, and publisher validation.
Security-aware development habits
Developers should treat extensions with the same caution as they do package dependencies. Every new tool should be vetted, especially when working with sensitive environments.
Proactive auditing of local environments
Security teams must monitor developer tools and extensions with the same scrutiny applied to binaries, scripts, or browser plugins.
Bottom Line
Security isn't just a step in your pipeline.
It doesn't start with code reviews or CI builds.
It starts with your editor.
Whether writing your first line of code or evaluating your next tool, vigilance is critical. Because sometimes, the compromise begins before the first bug is written.
References
VS Code extensions found downloading early-stage ransomware
Malicious helpers: VS Code Extensions observed stealing sensitive information | ReversingLabs
VS Code Marketplace Removes Two Extensions Deploying Early-Stage Ransomware


